 Greetings friends, a few days ago I was showing you everything we need to know about Veeam Backup for AWS v2, in case you haven’t been paying attention, I’m posting the blog here (in Spanish):
Greetings friends, a few days ago I was showing you everything we need to know about Veeam Backup for AWS v2, in case you haven’t been paying attention, I’m posting the blog here (in Spanish):
Today I bring you one more step on how to correctly secure our instance of Veeam Backup for AWS v2.
To do this we will rely on Let’s Encrypt, the famous open-source project that allows us to generate free SSL certificates.
NOTE: This process is not officially supported by Veeam, and any consequence of following the steps incorrectly, or any incidence derived from these steps will leave us without support. We will have to deploy the appliance again, keep that in mind!
Installation of system requirements
To make it all work we’re going to need a couple of packages to do all this automatically:
- jq
- The necessary Let’s Encrypt packages
To install jq, we will launch the following command:
sudo apt-get install jq -y
Once we have jq, we will now install the Let’s Encrypt packages, which is as simple as launching the following:
cd /root curl https://get.acme.sh | sh
This will create the following directory with the following in it:
ls .acme.sh/ -lah total 240K drwx------ 8 root root 4.0K May 15 10:44 . drwx------ 5 root root 4.0K May 15 12:32 .. -rw-r--r-- 1 root root 345 May 15 12:33 account.conf -rwxr-xr-x 1 root root 193K May 15 09:36 acme.sh -rw-r--r-- 1 root root 78 May 15 09:36 acme.sh.env drwxr-xr-x 3 root root 4.0K May 15 10:44 ca drwxr-xr-x 2 root root 4.0K May 15 09:36 deploy drwxr-xr-x 2 root root 4.0K May 15 09:36 dnsapi -rw-r--r-- 1 root root 332 May 15 14:49 http.header drwxr-xr-x 2 root root 4.0K May 15 09:36 notify
We’re all set. Let’s move on to the next step.
Download, and configure the veeam_aws_ssl.sh script
I have created a script that what it really does is combine with the Let’s Encrypt Script, and install the SSL Certificate in Veeam Backup for AWS, which needs to be converted to .pfx, but this does all the script, we will download it from here, I would put it in /root too, or in the same folder where we have downloaded Let’s Encrypt:
There are a few parameters to be set, but they are not difficult, let’s see them here:
- veeamDomain: This is the FQDN of your VBA, for example – vba.domain.com
- veeamSSLPassword: A password to encrypt the .pfx certificate
- veeamUsername: The user with access to the Veeam Backup for AWS v2 RESTFul API
- veeamPassword: The password for the user with access to the Veeam Backup for Microsoft AWS v2 RESTFul API
- veeamBackupAWSServer: The Public IP of the Veeam Backup for AWS v2
# Configurations ## # Endpoint URL for login action veeamDomain="YOURVEEAMAWSAPPLIANCEDOMAIN" veeamSSLPassword="YOURVEEAMSSLPASSWORD" #Introduce a password that will be use to merge the SSL into a .PFX veeamOutputPFXPath="/tmp/bundle.pfx" veeamUsername="YOURVEEAMBACKUPUSER" veeamPassword="YOURVEEAMBACKUPPASS" veeamBackupAWSServer="https://YOURVEEAMBACKUPIP" veeamBackupAWSPort="11005" #Default Port
Once we have everything filled in, we can exit the text editor and continue with the next step.
Launching Let’s Encrypt and getting a SSL certificate
Now that we have our script ready, and also Let’s Encrypt, it’s time to launch the Let’s Encrypt command, as you know, the command can be launched with several verification modes, in this case, I’m going to use Cloudflare, but it would also work with standalone, etc. See more here about the methods there are:
The script I created will look inside /root/.acme.sh/YOURFQDN, so as long as everything is in this directory, it will work, let’s see how I used Cloudflare.
cd /root export CF_Key="YOURCLOUDFLAREKEY" export CF_Email="[email protected]" # Email address we use in CloudFlare .acme.sh/acme.sh --issue -d YOURBA.DOMAIN.COM --dns dns_cf --reloadcmd "/root/veeam_aws_ssl.sh" --force
To know your Key de Cloudflare, here where you can find it
 Once we launch this command well, we will be able to see a result similar to this:
Once we launch this command well, we will be able to see a result similar to this:
[Sun Jun 21 11:38:36 UTC 2020] Single domain='vbaws.jorgedelacruz.es' [Sun Jun 21 11:38:36 UTC 2020] Getting domain auth token for each domain [Sun Jun 21 11:38:37 UTC 2020] Getting webroot for domain='vbaws.jorgedelacruz.es' [Sun Jun 21 11:38:37 UTC 2020] vbaws.jorgedelacruz.es is already verified, skip dns-01. [Sun Jun 21 11:38:37 UTC 2020] Verify finished, start to sign. [Sun Jun 21 11:38:37 UTC 2020] Lets finalize the order, Le_OrderFinalize: https://acme-v02.api.letsencrypt.org/acme/finalize/89380917/3863053238 [Sun Jun 21 11:38:38 UTC 2020] Download cert, Le_LinkCert: https://acme-v02.api.letsencrypt.org/acme/cert/045600bfd0d43d58bb1c832bf4b755a51429 [Sun Jun 21 11:38:40 UTC 2020] Cert success. -----BEGIN CERTIFICATE----- MIIFZDCCBEygAwIBAgISBFYAv9DUPVi7HIMr9LdVpRQpMA0GCSqGSIb3DQEBCwUA MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0yMDA2MjExMDM4MzhaFw0y [...] TNorQsk2U8SsLAxERvXjV460ni0ryjeuBQp+7mhAmuPSOa+FHDJWOx0ntmDWKwyD GtaUTA9HIqk577fJqNypUfMYNwdMCv9i4FCQTF3pqNGC3+ix6IrI4A== -----END CERTIFICATE----- [Sun Jun 21 11:38:40 UTC 2020] Your cert is in /root/.acme.sh/vbaws.jorgedelacruz.es/vbaws.jorgedelacruz.es.cer [Sun Jun 21 11:38:40 UTC 2020] Your cert key is in /root/.acme.sh/vbaws.jorgedelacruz.es/vbaws.jorgedelacruz.es.key [Sun Jun 21 11:38:40 UTC 2020] The intermediate CA cert is in /root/.acme.sh/vbaws.jorgedelacruz.es/ca.cer [Sun Jun 21 11:38:40 UTC 2020] And the full chain certs is there: /root/.acme.sh/vbaws.jorgedelacruz.es/fullchain.cer [Sun Jun 21 11:38:40 UTC 2020] Run reload cmd: /root/veeam_aws_ssl.sh Your Veeam Backup for AWS SSL Certificate has been replaced with a valid Let's Encrypt one. Go to https://vbaws.jorgedelacruz.es [Sun Jun 21 11:38:43 UTC 2020] Reload success
And if everything has gone well, we will have the little message that tells us that we can go to our https://YOURFQDN, if we go we can finally see the next thing: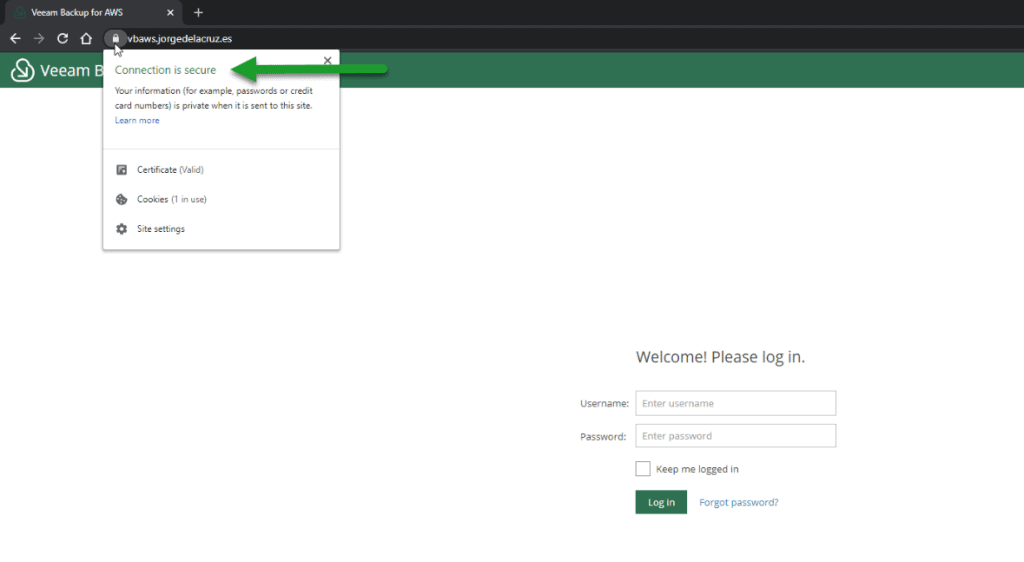
If we expand the SSL Certificate, we will be able to see which FQDN has assigned this SSL Certificate to us: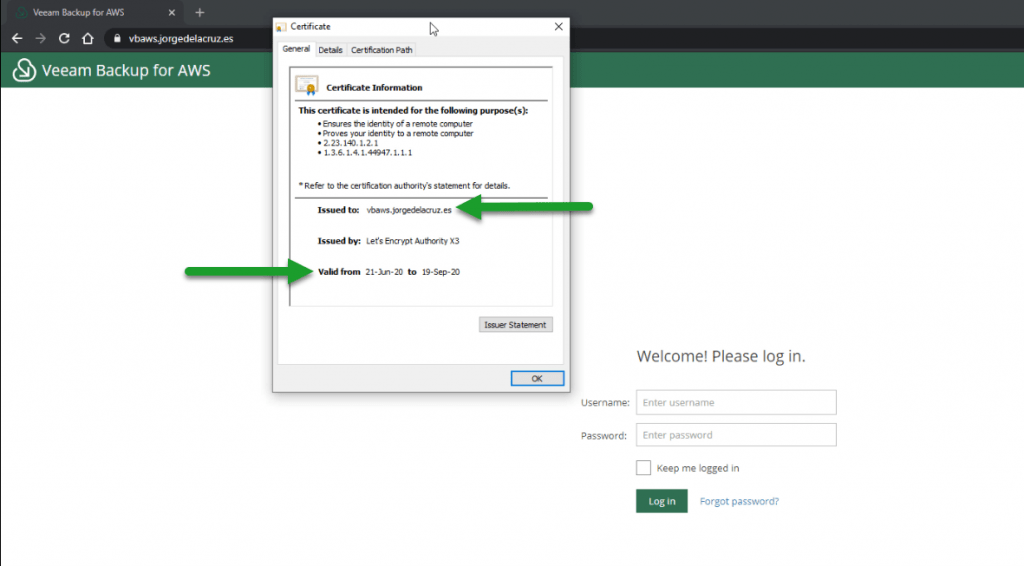
How to schedule the automated renewal to run every 90 days
These SSL Certificates expire every 90 days, so we can schedule it with the next command, and have a valid SSL certificate forever, as long as this scheduled task is executed:
* * */89 * * .acme.sh/acme.sh --issue -d YOURFQDN.DOMAIN.COM --dns dns_cf --reloadcmd "/root/veeam_aws_ssl.sh" --force > /var/log/syslog
With this, we’d be all set. Leave comments and ideas in the comments. Thank you for reading it.

Leave a Reply