 Greetings friends, a few days ago, I’ve prepared a really detailed Blog post with the release of Veeam Backup for Microsoft 365 v6. I have received around dozen messages, either via LinkedIn, or even internal colleagues asking how to enable the Restore Portal (self-service). So I have decided to document the required steps to enable a key functionality like this.
Greetings friends, a few days ago, I’ve prepared a really detailed Blog post with the release of Veeam Backup for Microsoft 365 v6. I have received around dozen messages, either via LinkedIn, or even internal colleagues asking how to enable the Restore Portal (self-service). So I have decided to document the required steps to enable a key functionality like this.
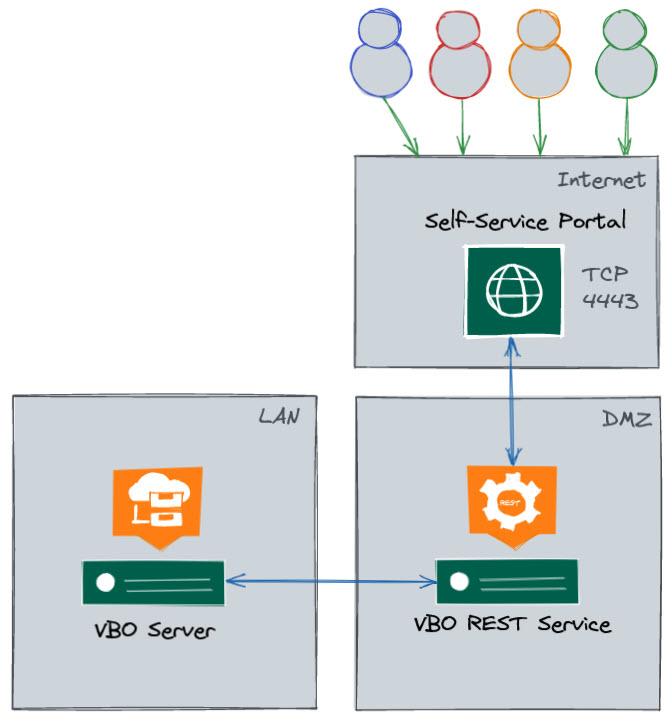
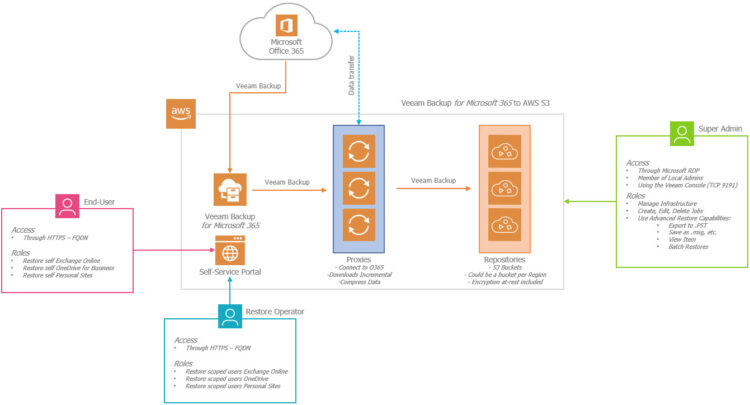
What does the Topology look like for a big environment using Restore Portal?
The moving parts that will take action on the Restore Portal are the next:
- Veeam Backup for Microsoft 365 server
- Veeam Backup for Microsoft 365 RESTful API Service
- Microsoft 365 organization
- Restore Portal
- Veeam Backup Proxy for Microsoft 365 Service
One of the important things to understand is that the components are meant to be distributed in order to scale out the design. (Please note I have not added Repositories or Proxies to this diagram, it is just for Self-Service Portal).
For example, this diagram shows a very high-level design with three moving parts, the VBM Server itself, usually on a protected Network like LAN, and then the VBM RESTful API + Restore Portal, which is on a public-facing network. The Restore Portal and the REST API components are always together.
 For a bit smaller environments, you would be able to put all the services together, and perhaps add the Proxy/Repo on other computers. However, please be mindful that the System Requirements have changed and now as a minimum, the VBM 365 Server needs to have 8CPU/16GB RAM.
For a bit smaller environments, you would be able to put all the services together, and perhaps add the Proxy/Repo on other computers. However, please be mindful that the System Requirements have changed and now as a minimum, the VBM 365 Server needs to have 8CPU/16GB RAM.
If I was deploying this into production, and a couple of hundred users would have access to the Restore Portal, I would be doing it already in a multi-server mode, 1 VBM365, 1RESTAPI+RestorePortal, X Proxies. I mean, we are exposing a 443 to the Internet, which is by default using a DMZ.
How-to Enable Veeam Backup for Microsoft 365 Restore Portal
Enable the new Restore Portal takes a few seconds, it just needs to be in a particular order, everything needs to be done from the Options menu:
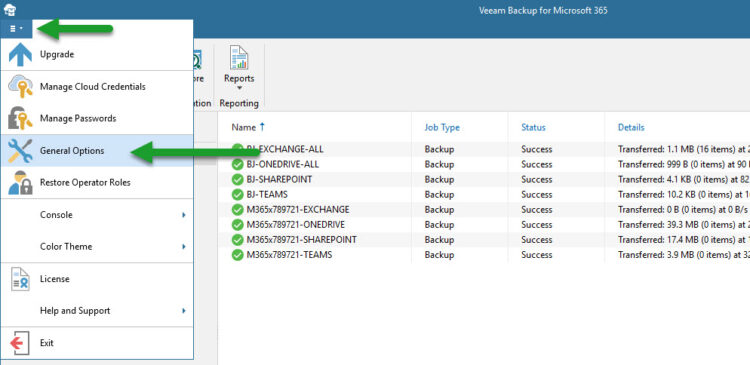
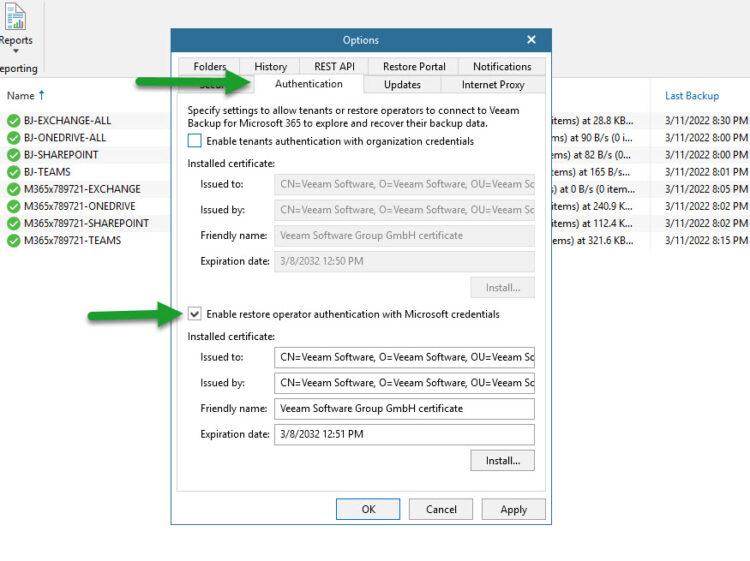
- General Options – Authentication – Enable Restore Operator Authentication with Microsoft credentials + click Install on the SSL and produce a self-signed

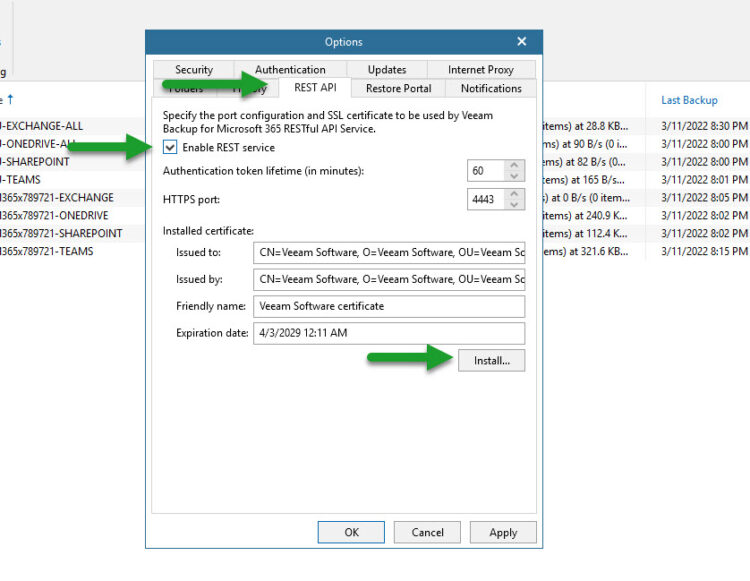
- Options – REST API – Enable REST service + click Install on the SSL and produce a self-signed (this is the one that it will get exposed to the clients, so a valid commercial SSL is always better to avoid calls, dramas, and “insecure look”)

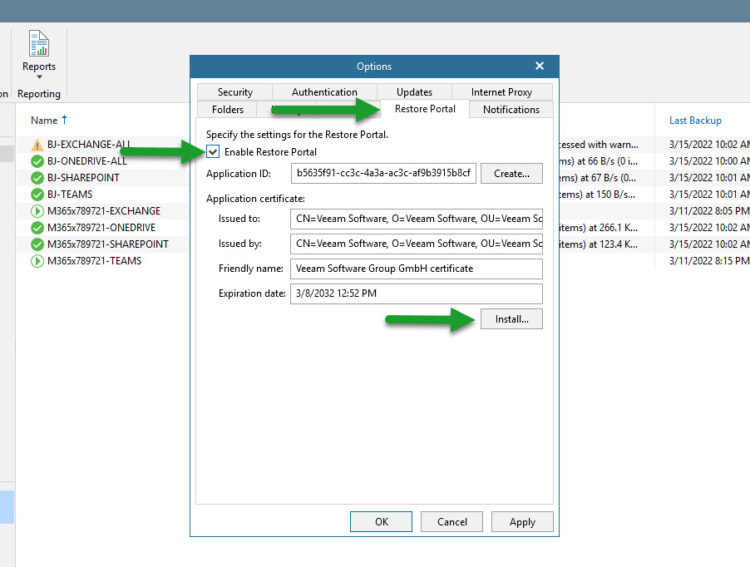
- Options – Restore Portal – Enable Restore Portal + click Install on the SSL and produce a self-signed

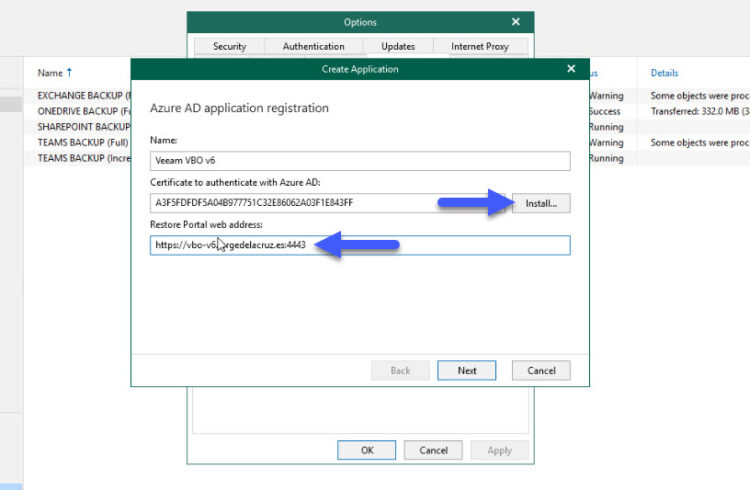
- On the same tab, now Create Application, Name whatever you like + click Install on the SSL and produce a self-signed + Restore Portal web address, it needs to be like this https://yourvbofqdn:4443 – this is not your Azure Organization, neither your Office 365 domain tenant, this is the FQDN you want your clients to access, on my case for example it is https://vbo-v6.jorgedelacruz.es:4443 and on my browser, I can access that URL

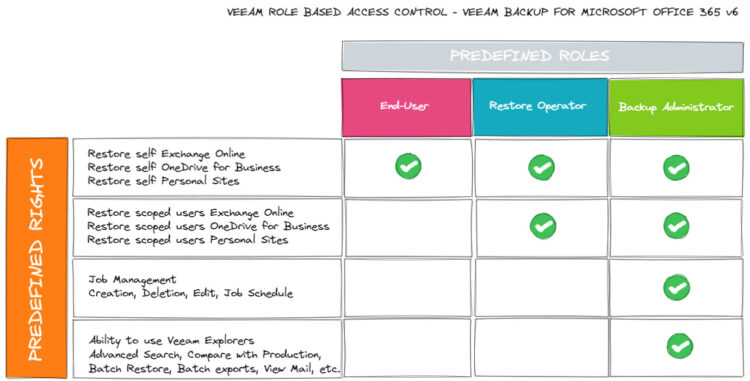
Role-based access control on Veeam Backup for Microsoft 365 v6
According to Wikipedia:
In computer systems security, role-based access control (RBAC)[1][2] or role-based security[3] is an approach to restricting system access to authorized users. It is an approach to implement mandatory access control (MAC) or discretionary access control (DAC).
Role-based access control (RBAC) is a policy-neutral access-control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments.
So, based on this description, this is my personal opinion, I will say that Veeam Backup for Microsoft 365 v6 will allow RBAC, how?, I understand it like this:
A real-life example of Role-based access control on Veeam Backup for Microsoft 365 v6
If you want to see it on a diagram, with a bit more security, imagine we deploy the Veam Backup for Microsoft 365 on a Cloud Provider, like AWS, or Azure. Good practice across the different roles, access to perhaps a jumping box, etc. Hope this diagram helps you to understand a bit more the importance of different roles, etc.
Restore Operator Role
Tied to the previous functionality, of course, there is a new option on the Console called Restore Operator. This option will allow your organization to select specific individuals, or groups, once you have the groups, you can give them the scope they can restore when logging into the Self-Service Portal.
How-to Configure the Restore Operator Role
As per usual on any Veeam interface, just a few clicks and you are done, from the main console, click the main menu, then click Restore operator roles:
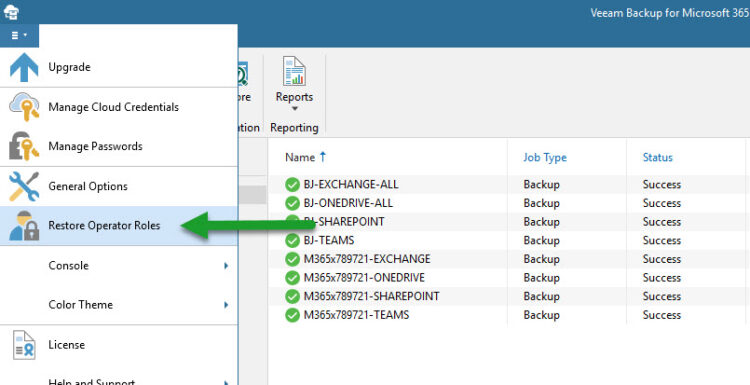
Kindly select the option Add restore operator roles:
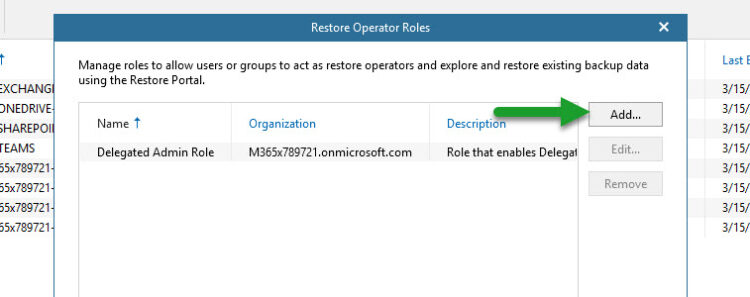
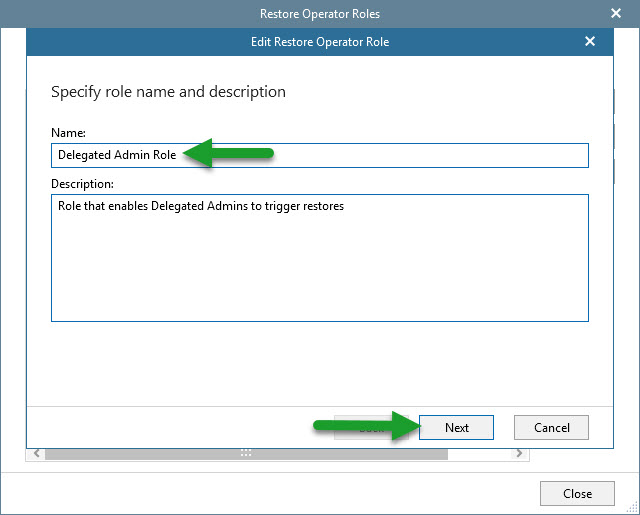
Let’s introduce a name for this specific role, on my case I have selected for example Delegated Admin Role:
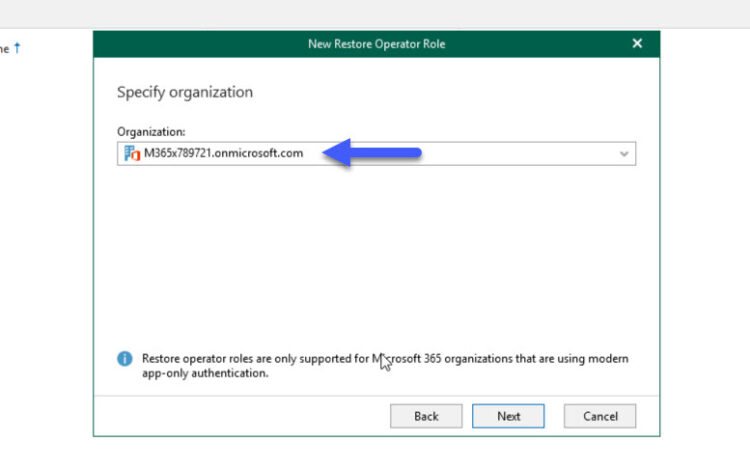
We can be granular and create different roles, for different Organizations (you might guess that this will be perfect for VCSP):
 Then we will select the Restore Operator or Group of Restore Operators:
Then we will select the Restore Operator or Group of Restore Operators:
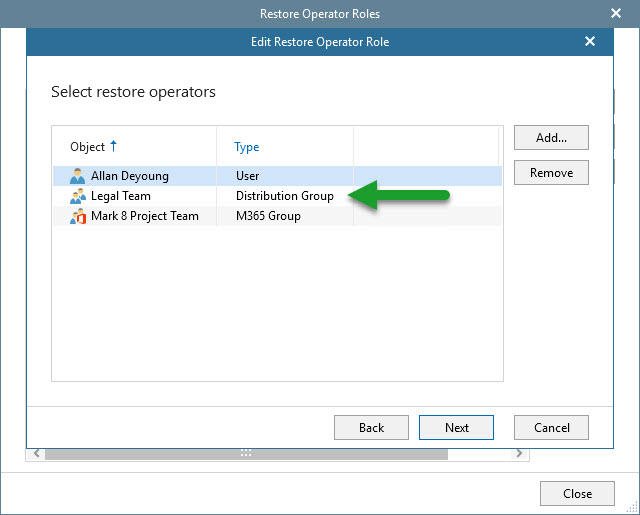
And give them the scope we require, a few SharePoint Sites, maybe some users, some groups, maybe some OneDrives, etc.
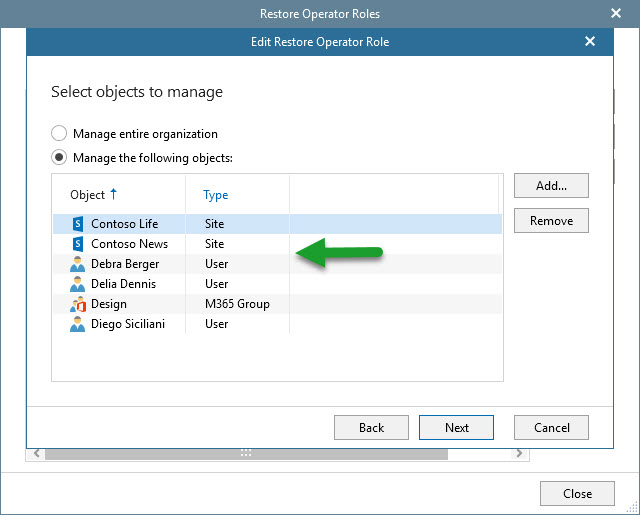
And that’s it, now we have a new Restore Operator Role created, we can create as many as we need. Once one of the Restore Operators login the Self-service portal, it will be available his/her own content, and the content that he/she has scope to restore as well.
Accessing the Restore Portal, and switching between the Scopes
If we head now to the FQDN we introduced when enabling the Restore Portal, we should see something similar to this:
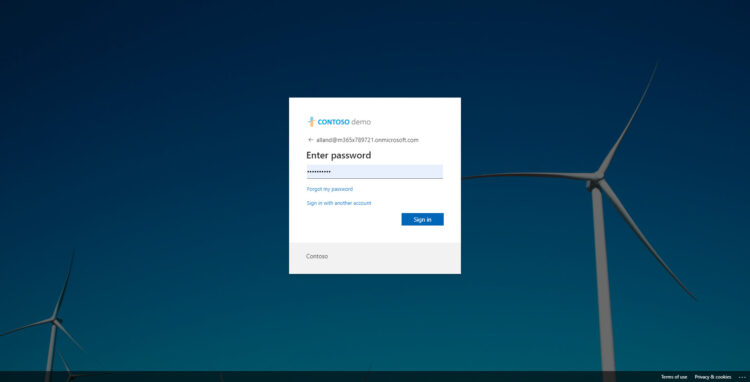
When we introduce valid credentials, that means a user, or Restore Operator that Veeam Backup for Microsoft 365 v6 is protecting, it will automatically redirect to the Microsoft AD Auth, if it has MFA, it will ask for it, etc. Veeam Backup for Microsoft 365 v6 relies on that authentication to access the backups of that user or scope, or not.
If all happens without any issue, what the user will see next, is his/her own Mailbox Backup, OneDrive, and Personal Sites, and it can recover from the last valid restore point, back to his/her own Mailbox, to another folder, etc.
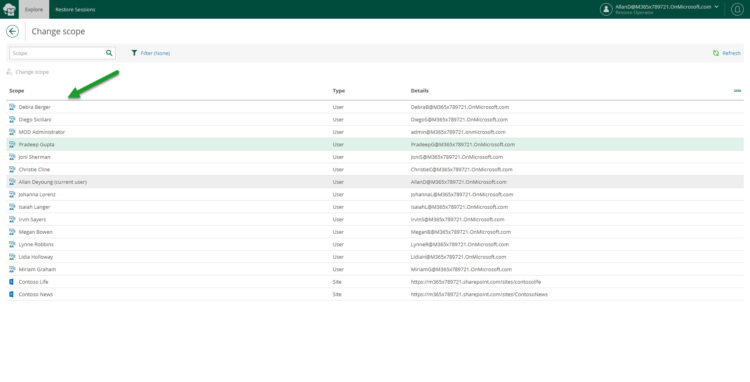
How does a Restore Operator switch between Scopes?
It is quite simple, on the top right, where the name of the user is, and only if they have assigned a Restore Operator Role with a Scope, then the next option will appear:
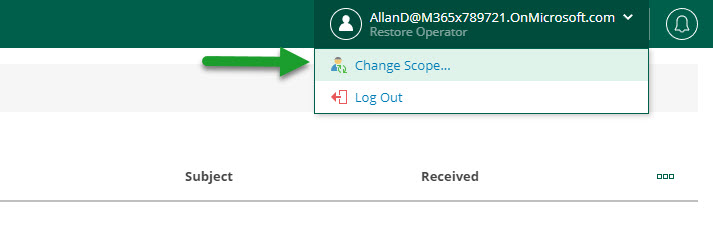
From here, a table with all the objects this user has Scope to restore will appear:

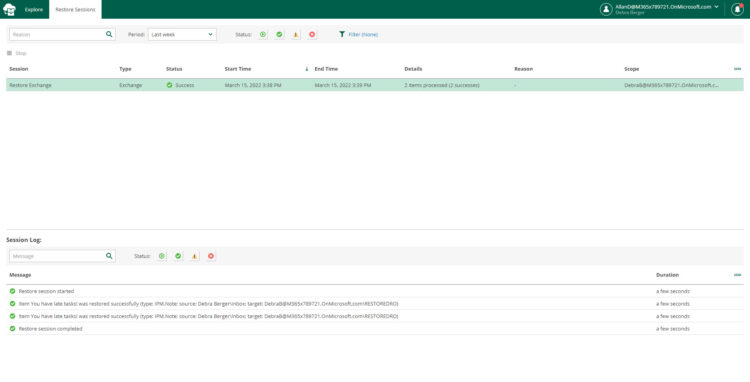
But do not worry, the Restore Operator can not export any of the files, or restore them to another user, etc. The Restore Operator Role could only restore back to the self-contained user/site it is accessing.
This will be an example of what the Restore Operator will see, or for that matters, any user triggering restores really:
Extra: Restore Portal loads, but when introducing valid user/pass appears AADSTS50011 – The Redirect URI error
This is a simple, but sadly a common mistake, and it is related to the point when we create the Restore Portal, to what URL/FQDN we use. As an example:
- I have created the Restore Portal with https://vbov6.jorgedelacruz.es:4443
- An experienced user that knows the IP of that server tries to open the Restore Portal using https://IPOFMACHINE:4443 <– They will see this error
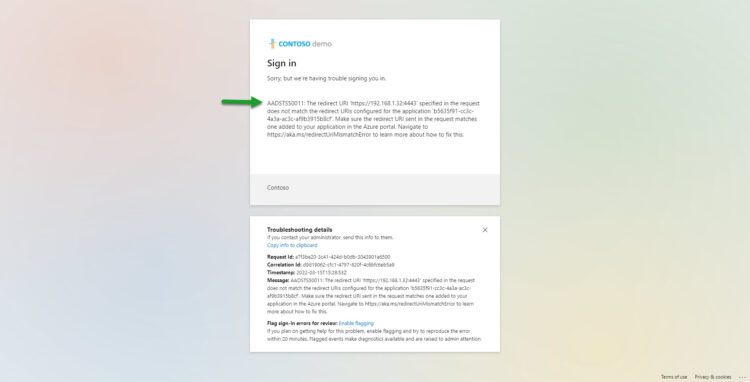
Issues like this are simple to debug, just use the very same FQDN used to create the Restore Portal, if in doubt. You can create the Restore Portal App as many times as you need 🙂
I hope you like this blog entry, and it is useful for you.

Thanks Jorge! Looking forward to part 2, Setting up the Service Principal in Azure AD for VB365 environments with multiple M365 tenants.
Thanks Jorge, We also look forward to Part 2 🙂
Thank you Jorge, very well written article!
Thank you, Jose,
Hope to see you soon at some of the events.
Best regards
Thanks!! Question: Why using AD authentication instead of Organisation?
On which step, Tomas?
Already finished the second part, will be published Monday at 08.15am
Hi Jorge,
Thank you very much for your series of articles about the new portal.
Just one thing: Do you know, if there is a way to redesign the portal (whitelabel it)?
We would like to use out company’s design for the portal, if possible.
Best regards from Germany,
Caroline
Good afternoon Caroline,
So, I have been messing around and found a few “hacks” to edit the logos, and some colors, but as said there are really hacks that I am assuming they will not be supported officially by Veeam.
Let me ask!
Thanks for reading, and commenting as well.
Hi Jorge
I have really enjoyed reading a few of your blogs, we are a Veeam service provider and provide 365 BaaS, and I am in the process of investigating configuring the self-service portal after I’ve recently upgraded it to version 6a. However, I am looking at the section of enabling the Restore Portal in the General Options, and I am unsure of who’s account I should be using to authenticate with Microsoft 365, as obviously, we have multiple tenants including our own tenancy. I’ve authenticated it with our GA account for our own tenancy, but how does this work with multi-tenancy?
I look forward to hearing your reply.
Kind regards
Stacey
Hello,
I’ve covered those steps in another blog post, but to find the entire list of articles, which includes SSL, adding additional URLs, etc. Please take a look here – https://community.veeam.com/discussion-boards-66/vb365-a-collection-of-fines-herbes-2430
Thank you so much; please do not hesitate to ping me with any questions you might have.
Hi Jorge,
Thanks for these tips it has been a great help in getting the self-service portal enabled. However, I am unable to access the portal URL on any device other than the server with the rest api on. Any tips on how to get this working would be appreciated.
Thanks!
Hello,
Well, the URL should be an FQDN right? like https://myvbserver.domain.co.uk:4443 which resolves to an IP. The external devices should use a DNS that tells them exactly that, that FQDN resolves to an IP, in the case that you are utside your network could be resolving to 80.90.40.70 or whatever public IP you have for that server, and you should be doing NAT of the port 4443 on your Router/Firewall. Besides that, well the usual Windows Firewall on the machine.
Great article. I also reviewed the video below, also posted from Veeam. One of the steps they discuss is having the customer run a Powershell script to add the appropriate application ID to their Azure portal. Is that not necessary if we follow your recommended steps above? We have a VCSP setup, where we are managing Veeam/O365 backups for multiple customers/organizations. Thanks.
https://community.veeam.com/blogs-and-podcasts-57/veeam-backup-for-microsoft-365-self-service-portal-multi-tenant-setup-2447
Hello,
You can follow those steps or the ones by images and text here – https://jorgedelacruz.uk/2022/03/21/veeam-how-to-enable-multi-tenant-on-the-new-restore-portal-on-veeam-backup-for-microsoft-365-v6/
You will still need to auth on the different tenants to enable the self-service. And I am sure this other blog post could be useful too, in case you want to offer to your tenants something like https://portal.theirowndomain.com instead of your generic URL – https://jorgedelacruz.uk/2022/03/24/veeam-how-to-add-new-urls-to-be-able-to-login-on-the-new-restore-portal-from-veeam-backup-for-microsoft-365-v6/
Good luck!