 Greetings friends, for many years, changing or adding an SSL certificate to our VMware vCenter has been a real pain, there are tens of KB, and hundreds of posts in the Community with errors of all kinds once you flirt with the steps. But from 6.7 onwards it seems that the process has been simplified a lot, so today I come to show you the steps to install your own SSL Certificate in VCSA, which is also free created with ZeroSSL. After the Let’s Encrypt drama with the CA expiring, and so on, I’ve decided to go and explore other 90 days free alternatives and I came across ZeroSSL, so let’s dive into it.
Greetings friends, for many years, changing or adding an SSL certificate to our VMware vCenter has been a real pain, there are tens of KB, and hundreds of posts in the Community with errors of all kinds once you flirt with the steps. But from 6.7 onwards it seems that the process has been simplified a lot, so today I come to show you the steps to install your own SSL Certificate in VCSA, which is also free created with ZeroSSL. After the Let’s Encrypt drama with the CA expiring, and so on, I’ve decided to go and explore other 90 days free alternatives and I came across ZeroSSL, so let’s dive into it.
How to request a free 90-day ZeroSSL Certificate
Let’s start by registering an account with them, they do not ask for more than an email and a password, which is always nice. Once we have the account created, we can go to create new certificate:
We should introduce our valid FQDN from our vCenter, on my case you can clearly see that I am requesting an SSL certificate for an FQDN called vcsa-7.jorgedelacruz.es, click in Next Step: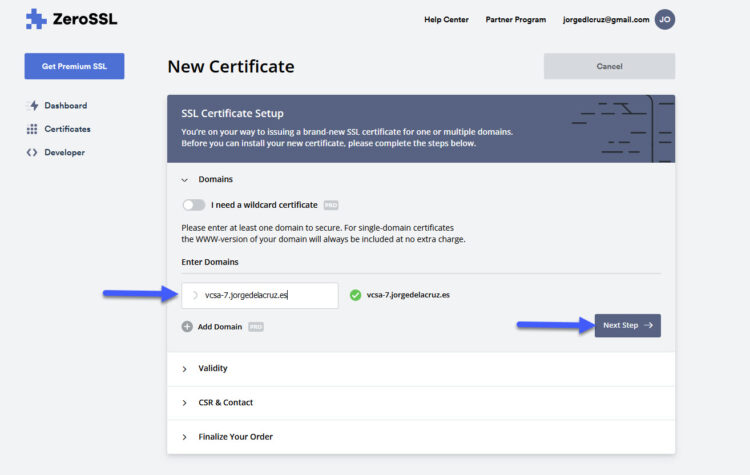
We need to make sure that we select just 90-Day Certificate, which is the free one, select that and click in Next Step: 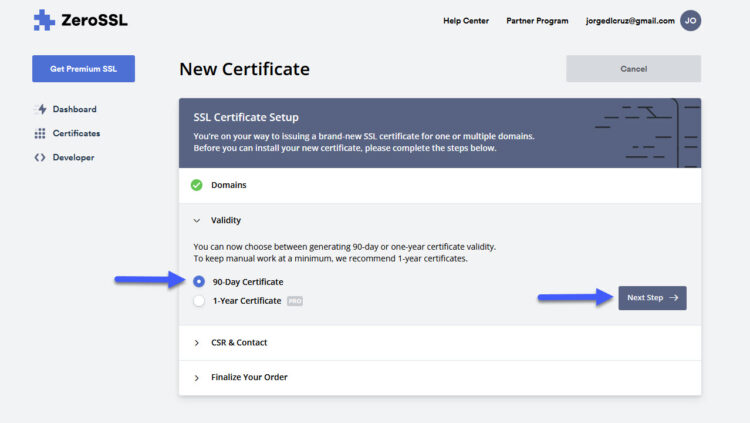
We are not going to create a CSR or anything from our vCenter, so we can leave the default option and click in Next Step: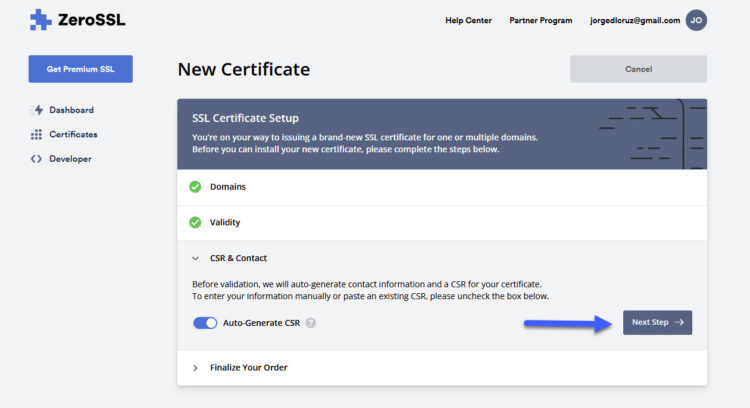
Just to make sure, make sure the Free option is selected, it would be if 90-day have been selected before, click Next Step: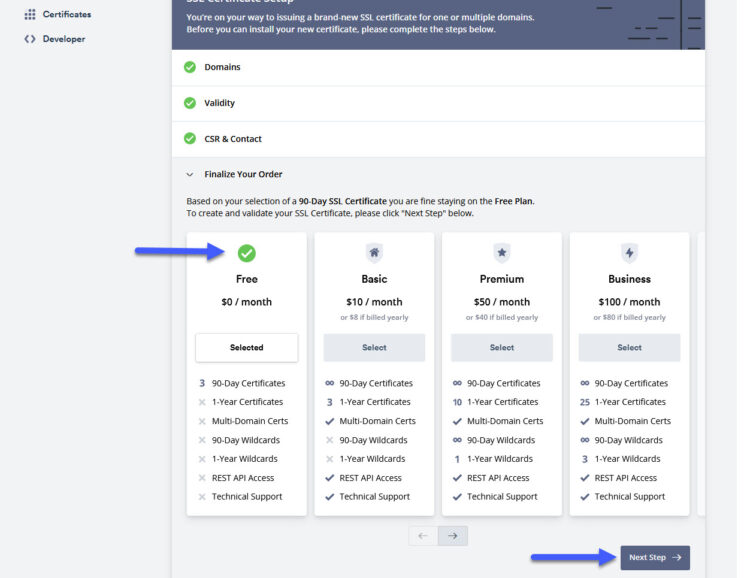
Now, we need to verify the FQDN, the domain, I usually prefer and like more a DNS with a CNAME, as I am using SplitDNS, meaning I have a jorgedelacruz.es DNS Zone for the Internet, which resolves my website, my mail, and others, to Public IPs, and my internal jorgedelacruz.es DNS Zone which resolves to my AD, my VMs, ESXi, VCSA, etc. As you can see here it is asking us to create a public CNAME, with a name, and with a point to, grab those two things: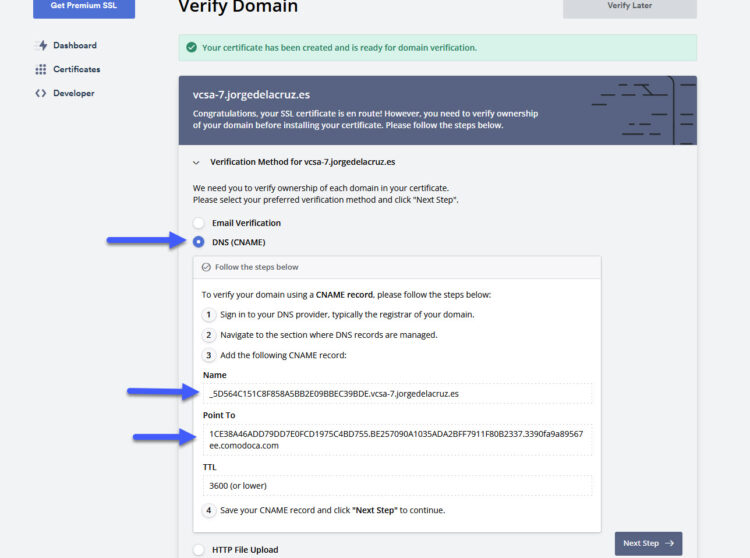
How to properly add the DNS requirements for ZeroSSL
Alright, so the first step will be to follow the requirement, and inside our public DNS, in my case it is Cloudflare, generate a new CNAME on my jorgedelacruz.es, like this (make sure the Proxy status is off):
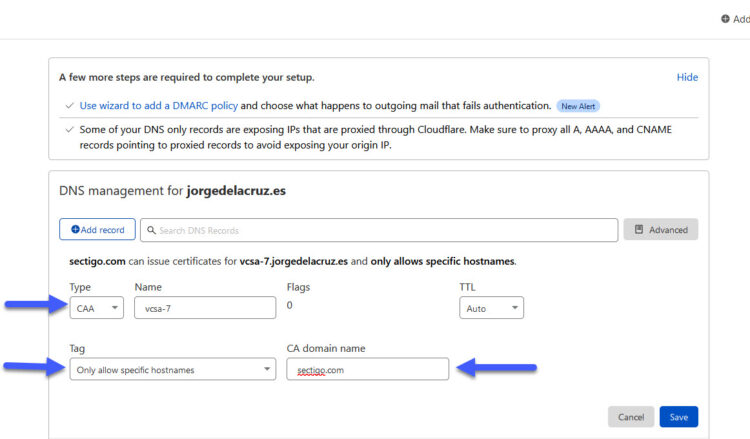
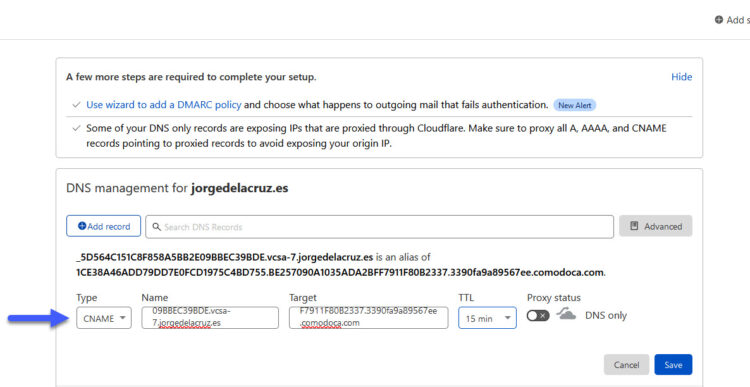 But this is not everything, ZeroSSL uses another DNS entry which is called CAA (A Certification Authority Authorization (CAA) record is used to specify which certificate authorities (CAs) are allowed to issue certificates), meaning we need to create a CAA entry pointing to what ZeroSSL recommends, it will look like this (you need to create an entry to your FQDN, pointing to sectigo.com, with the Tag Only allow specific hostnames better, type CAA remember:
But this is not everything, ZeroSSL uses another DNS entry which is called CAA (A Certification Authority Authorization (CAA) record is used to specify which certificate authorities (CAs) are allowed to issue certificates), meaning we need to create a CAA entry pointing to what ZeroSSL recommends, it will look like this (you need to create an entry to your FQDN, pointing to sectigo.com, with the Tag Only allow specific hostnames better, type CAA remember:
Yes! You are almost done, we can go back to our ZeroSSL website and click on Verify Domain:
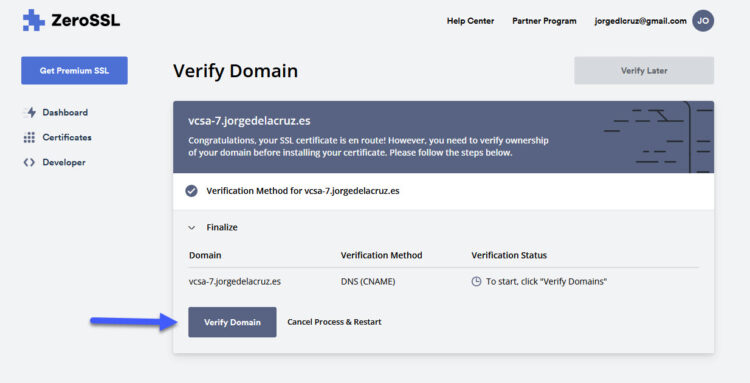 If you have introduced both DNS as described, you should see the next message, try a few times it fails, and comment here if it does not work:
If you have introduced both DNS as described, you should see the next message, try a few times it fails, and comment here if it does not work:
How to make VMware vCenter Server Appliance happy with an SSL certificate
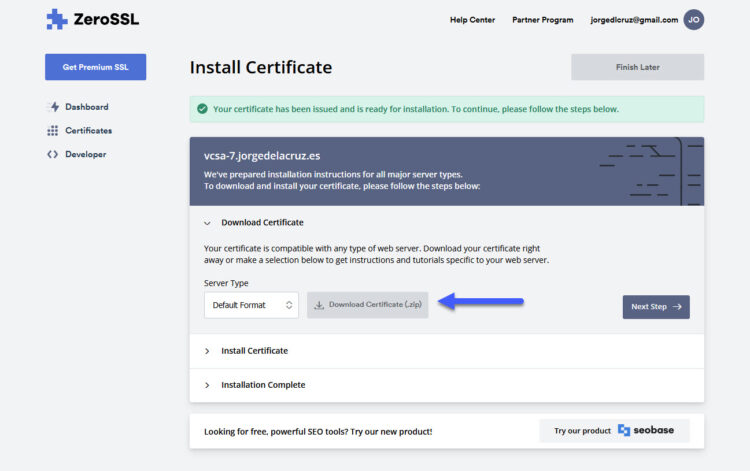
This is not an easy task, VMware VCSA it is extremely picky with the SSL certificates, it requires the Root Certificate to be inside the files in order to make it work. So at this point, from ZeroSSL you have three files:
- private.key
- certificate.crt
- ca_bundle.crt
You need to download the extra Root Certificate, at the moment of writing this have made the trick for me – https://crt.sh/?d=1282303295 but you can find a full page with more root certificates here – https://sectigo.com/knowledge-base/detail/Sectigo-Intermediate-Certificates/kA01N000000rfBO some other users have tried with the SHA-2 Root : USERTrust RSA Certification Authority on that website (it expires in 2038, so probably a good option)
But, what VMware is expecting? Let me explain, VMware will be absolutely happy, without errors, if you provide to it the next:
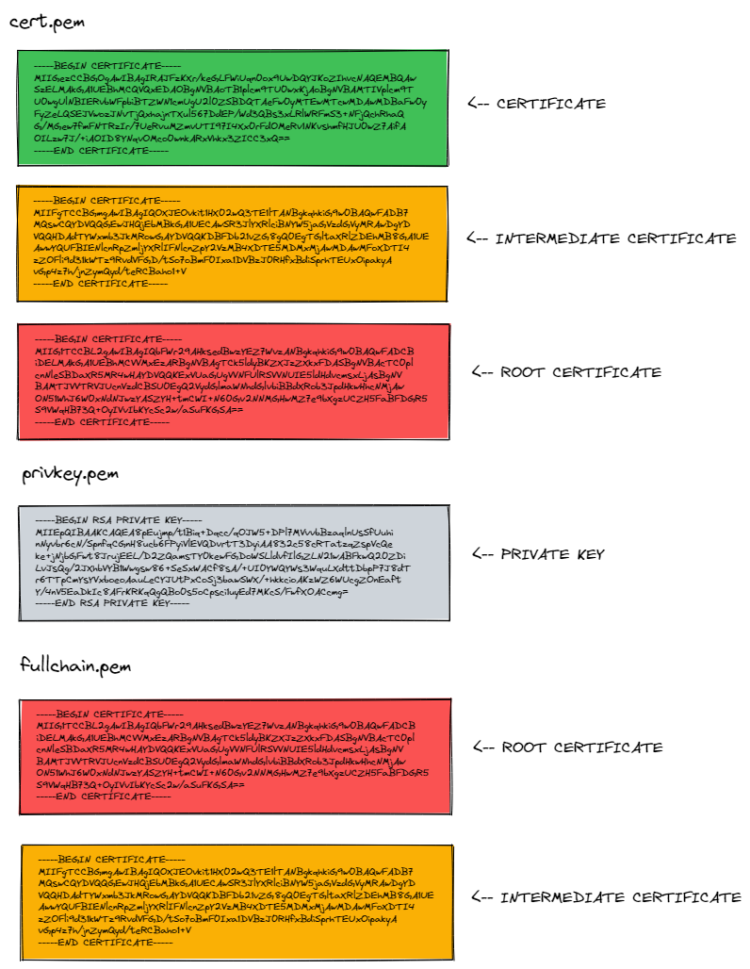 My fullchain.pem looks like this, just in case you want to copy-paste, as you can reuse it as you can see for the cert.pem as well, where you add it after the SSL certificate:
My fullchain.pem looks like this, just in case you want to copy-paste, as you can reuse it as you can see for the cert.pem as well, where you add it after the SSL certificate:
-----BEGIN CERTIFICATE----- MIIFgTCCBGmgAwIBAgIQOXJEOvkit1HX02wQ3TE1lTANBgkqhkiG9w0BAQwFADB7 MQswCQYDVQQGEwJHQjEbMBkGA1UECAwSR3JlYXRlciBNYW5jaGVzdGVyMRAwDgYD VQQHDAdTYWxmb3JkMRowGAYDVQQKDBFDb21vZG8gQ0EgTGltaXRlZDEhMB8GA1UE AwwYQUFBIENlcnRpZmljYXRlIFNlcnZpY2VzMB4XDTE5MDMxMjAwMDAwMFoXDTI4 MTIzMTIzNTk1OVowgYgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpOZXcgSmVyc2V5 MRQwEgYDVQQHEwtKZXJzZXkgQ2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBO ZXR3b3JrMS4wLAYDVQQDEyVVU0VSVHJ1c3QgUlNBIENlcnRpZmljYXRpb24gQXV0 aG9yaXR5MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAgBJlFzYOw9sI s9CsVw127c0n00ytUINh4qogTQktZAnczomfzD2p7PbPwdzx07HWezcoEStH2jnG vDoZtF+mvX2do2NCtnbyqTsrkfjib9DsFiCQCT7i6HTJGLSR1GJk23+jBvGIGGqQ Ijy8/hPwhxR79uQfjtTkUcYRZ0YIUcuGFFQ/vDP+fmyc/xadGL1RjjWmp2bIcmfb IWax1Jt4A8BQOujM8Ny8nkz+rwWWNR9XWrf/zvk9tyy29lTdyOcSOk2uTIq3XJq0 tyA9yn8iNK5+O2hmAUTnAU5GU5szYPeUvlM3kHND8zLDU+/bqv50TmnHa4xgk97E xwzf4TKuzJM7UXiVZ4vuPVb+DNBpDxsP8yUmazNt925H+nND5X4OpWaxKXwyhGNV icQNwZNUMBkTrNN9N6frXTpsNVzbQdcS2qlJC9/YgIoJk2KOtWbPJYjNhLixP6Q5 D9kCnusSTJV882sFqV4Wg8y4Z+LoE53MW4LTTLPtW//e5XOsIzstAL81VXQJSdhJ WBp/kjbmUZIO8yZ9HE0XvMnsQybQv0FfQKlERPSZ51eHnlAfV1SoPv10Yy+xUGUJ 5lhCLkMaTLTwJUdZ+gQek9QmRkpQgbLevni3/GcV4clXhB4PY9bpYrrWX1Uu6lzG KAgEJTm4Diup8kyXHAc/DVL17e8vgg8CAwEAAaOB8jCB7zAfBgNVHSMEGDAWgBSg EQojPpbxB+zirynvgqV/0DCktDAdBgNVHQ4EFgQUU3m/WqorSs9UgOHYm8Cd8rID ZsswDgYDVR0PAQH/BAQDAgGGMA8GA1UdEwEB/wQFMAMBAf8wEQYDVR0gBAowCDAG BgRVHSAAMEMGA1UdHwQ8MDowOKA2oDSGMmh0dHA6Ly9jcmwuY29tb2RvY2EuY29t L0FBQUNlcnRpZmljYXRlU2VydmljZXMuY3JsMDQGCCsGAQUFBwEBBCgwJjAkBggr BgEFBQcwAYYYaHR0cDovL29jc3AuY29tb2RvY2EuY29tMA0GCSqGSIb3DQEBDAUA A4IBAQAYh1HcdCE9nIrgJ7cz0C7M7PDmy14R3iJvm3WOnnL+5Nb+qh+cli3vA0p+ rvSNb3I8QzvAP+u431yqqcau8vzY7qN7Q/aGNnwU4M309z/+3ri0ivCRlv79Q2R+ /czSAaF9ffgZGclCKxO/WIu6pKJmBHaIkU4MiRTOok3JMrO66BQavHHxW/BBC5gA CiIDEOUMsfnNkjcZ7Tvx5Dq2+UUTJnWvu6rvP3t3O9LEApE9GQDTF1w52z97GA1F zZOFli9d31kWTz9RvdVFGD/tSo7oBmF0Ixa1DVBzJ0RHfxBdiSprhTEUxOipakyA vGp4z7h/jnZymQyd/teRCBaho1+V -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIG1TCCBL2gAwIBAgIQbFWr29AHksedBwzYEZ7WvzANBgkqhkiG9w0BAQwFADCB iDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0pl cnNleSBDaXR5MR4wHAYDVQQKExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNV BAMTJVVTRVJUcnVzdCBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMjAw MTMwMDAwMDAwWhcNMzAwMTI5MjM1OTU5WjBLMQswCQYDVQQGEwJBVDEQMA4GA1UE ChMHWmVyb1NTTDEqMCgGA1UEAxMhWmVyb1NTTCBSU0EgRG9tYWluIFNlY3VyZSBT aXRlIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhmlzfqO1Mdgj 4W3dpBPTVBX1AuvcAyG1fl0dUnw/MeueCWzRWTheZ35LVo91kLI3DDVaZKW+TBAs JBjEbYmMwcWSTWYCg5334SF0+ctDAsFxsX+rTDh9kSrG/4mp6OShubLaEIUJiZo4 t873TuSd0Wj5DWt3DtpAG8T35l/v+xrN8ub8PSSoX5Vkgw+jWf4KQtNvUFLDq8mF WhUnPL6jHAADXpvs4lTNYwOtx9yQtbpxwSt7QJY1+ICrmRJB6BuKRt/jfDJF9Jsc RQVlHIxQdKAJl7oaVnXgDkqtk2qddd3kCDXd74gv813G91z7CjsGyJ93oJIlNS3U gFbD6V54JMgZ3rSmotYbz98oZxX7MKbtCm1aJ/q+hTv2YK1yMxrnfcieKmOYBbFD hnW5O6RMA703dBK92j6XRN2EttLkQuujZgy+jXRKtaWMIlkNkWJmOiHmErQngHvt iNkIcjJumq1ddFX4iaTI40a6zgvIBtxFeDs2RfcaH73er7ctNUUqgQT5rFgJhMmF x76rQgB5OZUkodb5k2ex7P+Gu4J86bS15094UuYcV09hVeknmTh5Ex9CBKipLS2W 2wKBakf+aVYnNCU6S0nASqt2xrZpGC1v7v6DhuepyyJtn3qSV2PoBiU5Sql+aARp wUibQMGm44gjyNDqDlVp+ShLQlUH9x8CAwEAAaOCAXUwggFxMB8GA1UdIwQYMBaA FFN5v1qqK0rPVIDh2JvAnfKyA2bLMB0GA1UdDgQWBBTI2XhootkZaNU9ct5fCj7c tYaGpjAOBgNVHQ8BAf8EBAMCAYYwEgYDVR0TAQH/BAgwBgEB/wIBADAdBgNVHSUE FjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwIgYDVR0gBBswGTANBgsrBgEEAbIxAQIC TjAIBgZngQwBAgEwUAYDVR0fBEkwRzBFoEOgQYY/aHR0cDovL2NybC51c2VydHJ1 c3QuY29tL1VTRVJUcnVzdFJTQUNlcnRpZmljYXRpb25BdXRob3JpdHkuY3JsMHYG CCsGAQUFBwEBBGowaDA/BggrBgEFBQcwAoYzaHR0cDovL2NydC51c2VydHJ1c3Qu Y29tL1VTRVJUcnVzdFJTQUFkZFRydXN0Q0EuY3J0MCUGCCsGAQUFBzABhhlodHRw Oi8vb2NzcC51c2VydHJ1c3QuY29tMA0GCSqGSIb3DQEBDAUAA4ICAQAVDwoIzQDV ercT0eYqZjBNJ8VNWwVFlQOtZERqn5iWnEVaLZZdzxlbvz2Fx0ExUNuUEgYkIVM4 YocKkCQ7hO5noicoq/DrEYH5IuNcuW1I8JJZ9DLuB1fYvIHlZ2JG46iNbVKA3ygA Ez86RvDQlt2C494qqPVItRjrz9YlJEGT0DrttyApq0YLFDzf+Z1pkMhh7c+7fXeJ qmIhfJpduKc8HEQkYQQShen426S3H0JrIAbKcBCiyYFuOhfyvuwVCFDfFvrjADjd 4jX1uQXd161IyFRbm89s2Oj5oU1wDYz5sx+hoCuh6lSs+/uPuWomIq3y1GDFNafW +LsHBU16lQo5Q2yh25laQsKRgyPmMpHJ98edm6y2sHUabASmRHxvGiuwwE25aDU0 2SAeepyImJ2CzB80YG7WxlynHqNhpE7xfC7PzQlLgmfEHdU+tHFeQazRQnrFkW2W kqRGIq7cKRnyypvjPMkjeiV9lRdAM9fSJvsB3svUuu1coIG1xxI1yegoGM4r5QP4 RGIVvYaiI76C0djoSbQ/dkIUUXQuB8AL5jyH34g3BZaaXyvpmnV4ilppMXVAnAYG ON51WhJ6W0xNdNJwzYASZYH+tmCWI+N60Gv2NNMGHwMZ7e9bXgzUCZH5FaBFDGR5 S9VWqHB73Q+OyIVvIbKYcSc2w/aSuFKGSA== -----END CERTIFICATE-----
Install ZeroSSL SSL Certificate in VCSA with certificate-manager via shell
As we are still inside our VCSA by the shell, we can make use of the new certificate manager that is included in a few editions, to invoke it as simple as launching:
/usr/lib/vmware-vmca/bin/certificate-manager
That will show us the following menu, we will press 1:
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
| |
| *** Welcome to the vSphere 6.8 Certificate Manager *** |
| |
| -- Select Operation -- |
| |
| 1. Replace Machine SSL certificate with Custom Certificate |
| |
| 2. Replace VMCA Root certificate with Custom Signing |
| Certificate and replace all Certificates |
| |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| |
| 4. Regenerate a new VMCA Root Certificate and |
| replace all certificates |
| |
| 5. Replace Solution user certificates with |
| Custom Certificate |
| NOTE: Solution user certs will be deprecated in a future |
| release of vCenter. Refer to release notes for more details.|
| |
| 6. Replace Solution user certificates with VMCA certificates |
| |
| 7. Revert last performed operation by re-publishing old |
| certificates |
| |
| 8. Reset all Certificates |
|_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _|
Note : Use Ctrl-D to exit.
Option[1 to 8]: 1
This will ask us for credentials with permissions to operate the SSL Certificates within vsphere.local (or your SSO), in my case I will use administrator:
Please provide valid SSO and VC privileged user credential to perform certificate operations. Enter username [[email protected]]: Enter password:
Now we will select the second option to select our own SSL Certificate
1. Generate Certificate Signing Request(s) and Key(s) for Machine SSL certificate 2. Import custom certificate(s) and key(s) to replace existing Machine SSL certificate Option [1 or 2]: 2 Please provide valid custom certificate for Machine SSL. File : /root/cert.pem Please provide valid custom key for Machine SSL. File : /root/privkey.pem Please provide the signing certificate of the Machine SSL certificate File : /root/fullchain.pem
And we will already select yes in this last question, the services will be restarted automatically:
You are going to replace Machine SSL cert using custom cert Continue operation : Option[Y/N] ? : y Command Output: /root/cert.pem: OK Get site nameCompleted [Replacing Machine SSL Cert...] default-site Lookup all services Get service default-site:c528e353-4680-4885-9e07-6d1d5b5b632d Don't update service default-site:c528e353-4680-4885-9e07-6d1d5b5b632d Get service default-site:612774a5-5093-4eaa-892c-d5735d3af0fe ... Get service 9ae1be99-aabd-47a5-bd9a-f97f74eaf78f_com.vmware.vcenter.wcp Don't update service 9ae1be99-aabd-47a5-bd9a-f97f74eaf78f_com.vmware.vcenter.wcp Updated 0 service(s) Status : 100% Completed [All tasks completed successfully]
Check that our VCSA already has the new valid SSL Certificate
The moment of truth has arrived, we will go to our vCenter, remember that the certificate is only valid for the FQDN, if you access by IP it will always come out that it is not secure, and if it is the FQDN we will see the so desired green lock:
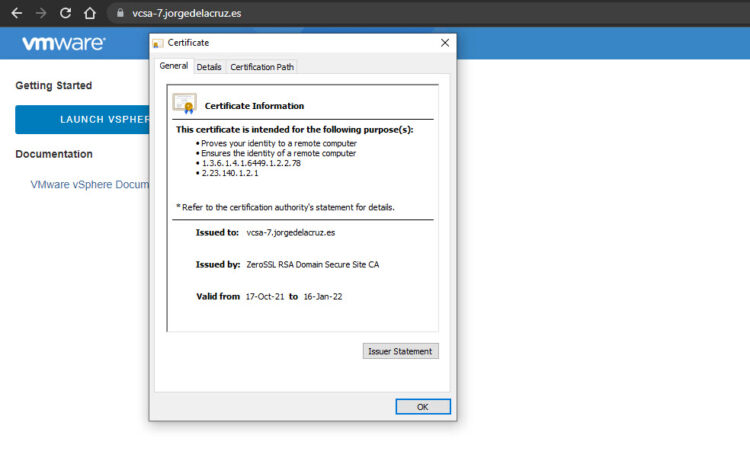
 In addition, we can see when the SSL certificate expires, properties, etc:
In addition, we can see when the SSL certificate expires, properties, etc:
 If we want to monitor our SSL Certificate to see when it expires so that we can renew it, I have a ticket for that:
If we want to monitor our SSL Certificate to see when it expires so that we can renew it, I have a ticket for that:
That’s all friends, I hope you like it and find it useful. A big greeting.

Thank you for this post. I was following your previous guide for using Let’s Encrypt and failing. In the end, I bought an SSL from Comodo and I used your incredibly useful image which shows how the certificates should be bundled and it worked first time using the web GUI! Didn’t even have to resort to command line.
The only issue I have is that Certificate Management page in vSphere Client, I get the warning “Error occurred while fetching machine certificates: com.vmware.vcenter.certificate_management.vcenter.tls” and it doesn’t show any of the certificates installed. It’s not a big deal but is that something you’ve seen? Perhaps it’s because of all the previous attempts to install an SSL!
Also do you know where the private key is stored? I used vSphere to generate the CSR so I want to make sure the private key is backed up to save me rekeying the SSL in the event of redeploying vSphere. Thanks!
THANK YOU VERY MUCH FOR THIS POST. I was going through the same issue as you had with letsencrypt (spent 50hrs with no luck).
Glad it helped, I have not gave up just yet on Let’s Encrypt maybe the new root 2 will help, but it is limited for now.
wondering if this could be automated with acme.sh? https://github.com/acmesh-official/acme.sh
been trying to get this to work with vcenter 7.0.3 but update manager is not happy.
Will give it a try later on, after multiple battles with let’s encrypt, then zerossl to the rescue, the last time it expired I came back into self-signed to avoid issues.
Will give it a try for sure.
Hi Folks.
Thanks to JorgeUK for all his tutos about SSL (Let’s Encrypt, ZeroSSL) and VCSA (6,7).
I’m trying to set up a free SSL certificate (nevermind the CA) with an automated renewal process on my 7.0.3 VCSA.
Dear Jorge, do you have a tuto for that ? 😉
Hello,
Which provider exactly, Gilou? Cheers
It seems ZeroSSL is the best choice at this moment: they offer (like you showed) free 3-monthes SSL certificates and I hope it will be possible to acme.sh for automatization…
thanks for your answer
Regards
Is this working for anyone on 7.0.3 Update 3j? Certificate Manager via CLI says that all certificates are replaced successfully, but Update Manager / Lifecycle Manager refuses to start after the certificate replacement…
Saved my life mate. Was ripping what’s left of my hair out! Cheers.
I’m not able to update the certs, stuck at 85%… I found some error in the logs:vpxd-svcs-runtime.log.stderr
org.apache.catalina.LifecycleException: Protocol handler initialization failed
Caused by: java.net.SocketException: Protocol family unavailable
Any idea why I get this?
That is very strange, what VCSA version? I would probably start from scratch, meaning putting self signed first again, and doing a cleanup:
https://jorgedelacruz.uk/2021/11/23/vmware-fixing-annoying-error-cannot-connect-to-profile-driven-storage-service-related-to-ssl-certificates/
Let us know
Do you have any solutions for 7.0.3? Looks like updatemgr does not start anymore with zerossl.