 Greetings everyone, as you might know by now, I tend to like to do a bit both, tell you about exciting new functionalities on the software, like a few days ago about Grafana 8.3, but why not if something is critical at the security level, I think it needs to be discussed as well, as I did with the VMware vulnerability (that eventually led to the removal of the ISO from the website – not related or based on my blog of course).
Greetings everyone, as you might know by now, I tend to like to do a bit both, tell you about exciting new functionalities on the software, like a few days ago about Grafana 8.3, but why not if something is critical at the security level, I think it needs to be discussed as well, as I did with the VMware vulnerability (that eventually led to the removal of the ISO from the website – not related or based on my blog of course).
Today I want to discuss, and to urge you to update to the latest Grafana release if you are in Grafana 8.x, as the guys are facing their very first 0-day vulnerability.
How-to check in which version we are
You have two different ways, the first one, quite simple, directly from the Web Browser on the login page, at the mid-bottom of the screen, you will see the next:
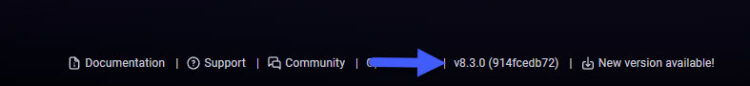 In the case that you are logged in already, just left bottom you will see the next:
In the case that you are logged in already, just left bottom you will see the next:
 A bit more sophisticated, and because we will need SSH access anyways, you can type the next on the shell to see as well:
A bit more sophisticated, and because we will need SSH access anyways, you can type the next on the shell to see as well:
grafana-server -v Version 8.3.0 (commit: 914fcedb72, branch: HEAD)
Alright, now that we know what version are we in, it is time to update.
How-to upgrade to the latest Grafana version
As per usual, you have two different ways, a few more in case you are using Containers, but let’s focus more on the vanilla installations if you have installed Grafana from the official repositories, as it should be really, as easy as:
sudo apt-get update && apt-get install --only-upgrade grafana
This will upgrade just that very package, without interfering much on the rest of the system, the output will be similar to this:
Hit:1 https://packages.grafana.com/oss/deb stable InRelease Hit:2 https://repos.influxdata.com/ubuntu focal InRelease Hit:3 http://gb.archive.ubuntu.com/ubuntu focal InRelease Get:4 http://gb.archive.ubuntu.com/ubuntu focal-updates InRelease [114 kB] Get:5 http://gb.archive.ubuntu.com/ubuntu focal-backports InRelease [108 kB] Get:6 http://gb.archive.ubuntu.com/ubuntu focal-security InRelease [114 kB] Get:7 http://gb.archive.ubuntu.com/ubuntu focal-updates/main amd64 Packages [1,391 kB] Get:8 http://gb.archive.ubuntu.com/ubuntu focal-updates/main Translation-en [282 kB] Get:9 http://gb.archive.ubuntu.com/ubuntu focal-updates/universe amd64 Packages [881 kB] Get:10 http://gb.archive.ubuntu.com/ubuntu focal-updates/universe Translation-en [191 kB] Get:11 http://gb.archive.ubuntu.com/ubuntu focal-security/universe amd64 Packages [665 kB] Get:12 http://gb.archive.ubuntu.com/ubuntu focal-security/universe Translation-en [111 kB] Fetched 3,857 kB in 1s (3,273 kB/s) Reading package lists... Done Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: apache2 apache2-bin apache2-data augeas-lenses libaprutil1-dbd-sqlite3 libaprutil1-ldap libaugeas0 libjansson4 liblua5.2-0 python3-acme python3-augeas python3-certbot python3-configargparse python3-future python3-icu python3-josepy python3-mock python3-parsedatetime python3-pbr python3-requests-toolbelt python3-rfc3339 python3-tz python3-zope.component python3-zope.event python3-zope.hookable Use 'sudo apt autoremove' to remove them. The following packages will be upgraded: grafana 1 upgraded, 0 newly installed, 0 to remove and 17 not upgraded. Need to get 73.1 MB of archives. After this operation, 0 B of additional disk space will be used. Get:1 https://packages.grafana.com/oss/deb stable/main amd64 grafana amd64 8.3.1 [73.1 MB] Fetched 73.1 MB in 2s (40.2 MB/s) (Reading database ... 133731 files and directories currently installed.) Preparing to unpack .../grafana_8.3.1_amd64.deb ... Unpacking grafana (8.3.1) over (8.3.0) ... Setting up grafana (8.3.1) ... Restarting grafana-server service... OK Processing triggers for systemd (245.4-4ubuntu3.13) ...
Let’s quickly check the version now:
grafana-server -v Version 8.3.1 (commit: 8d38082755, branch: HEAD)
Alright, we are now on the safe side, and we can breathe until the next critical one, hope it takes months. Good job!
A few more insights into the Grafana CVE-2021-43798
There is not a 100% secure software that does not have some vulnerabilities found from time to time, the software is made by people, and even if working extremely hard, sometimes these things will keep occurring, due to some coding mismatch, or some not really well-hardened access to some system files, or libraries, etc.
The Grafana team has released an impressive transparent timeline of what happened on the next blog post, what we can see on Jordy, who discovered the vulnerability, detailed blog about the incident, is as I’ve said before, a non very well protected Golan os.Open which opens system files.
In just a few days they had everything fixed, releases announced, and more important, seems that Grafana is about to release a bug bounty program, which for sure will make their impeccable product, even more, robust and secure with things like these. Hats off, Grafana.

Thanks Mom. 🙂
I’m on it!
sudo apt update; sudo apt install grafana