 Greetings, this topic is a very interesting one, the other day in the Veeam forums, a Customer asked if it was a simple way to retrieve the SSL Certificate Veeam uses for the Microsoft 365 Enterprise Application, as they recently had problems due expiration of their Certificate.
Greetings, this topic is a very interesting one, the other day in the Veeam forums, a Customer asked if it was a simple way to retrieve the SSL Certificate Veeam uses for the Microsoft 365 Enterprise Application, as they recently had problems due expiration of their Certificate.
Short answer is: nothing in the Veeam Backup for Microsoft 365 Console, UI, PowerShell, or API shows by default the expiration date of this SSL Certificate, or any other as VBM365 uses another two certificates.
But as usual, this blog post will cover an alternate way of how to retrieve the expiration date of the Veeam Backup for Microsoft 365 Enterprise Application Certificate, it works as well for the Restore Portal SSL Certificate for example. Let’s jump into the step by step.
Getting to know our Enterprise Application ID
First thing to check it will be out Enterprise Application ID, we can do this following three different ways, for example using the RESTful API:
curl -X GET --header 'Accept: application/json' --header 'Authorization: Bearer YOURTOKEN' 'https://YOURVB365Server:4443/v6/Organizations/YOURORGID/Applications'
Or if you are better within PowerShell, from the VB365 Server, we can save the Organization into a variable:
$vb365Org = Get-VBOOrganization -Name "M365x42552316.onmicrosoft.com"
And then get the Applications this specifig Organization has, on my case we can see it is the one called Veeam M365x42552316:
Get-VBOApplication -Organization $vb365Org
Id DisplayName Tags
-- ----------- ----
a5ed015c-4c75-459d-8837-33d4e1eeb3ac BrowserStack {}
8f19384e-ba23-4490-b375-3c0bebd3c7fd Veeam M365x42552316 {}
825bc308-9874-41b3-9604-9213c6994461 LinkedIn {}
79b7911f-c941-4362-b8da-7b389fd690cc Veeam Restore Portal v6a {}
6b354c37-5e80-4925-bb5b-2ed7ef3bca04 Box {}
5794cda7-9e4a-429d-942c-32d8eed7eb93 Salesforce {}
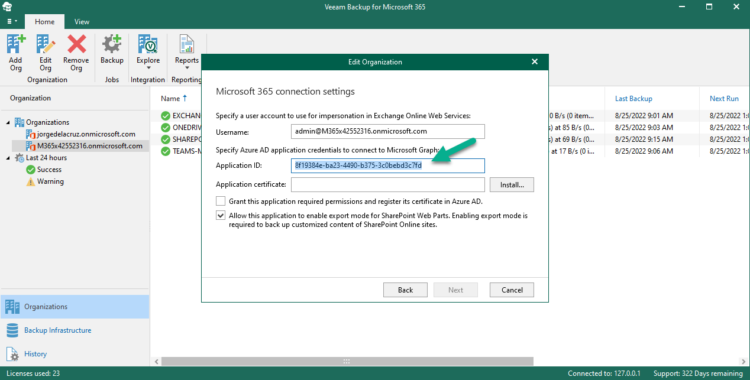
Another simpler option it might be just edit our Organization and grab the Application ID from there:
Back to Basics, How to Install Azure AD PowerShell Module
To check the different Enterprise Applications Certificates, we will make use of the AzureAD PowerShell Module, in order to install it, just as simple as:
Install-Module AzureAD Connect-AzureAD
This is going to ask for a valid credentials from our Tenant, it should have enough privileges in order to query the applications, etc.
How to check the Certificate information, including expiration date from an Enterprise Application
We are almost there, let’s save our Application ID to a variable, and let’s get the SSL Certificate (KeyCredentials) into another variable called appCert:
$appId = "8f19384e-ba23-4490-b375-3c0bebd3c7fd" $appCert = Get-AzureADApplication -Filter "AppId eq '$($appId)'" | select KeyCredentials
If we want to take a look to what information we have inside this variable as simple as:
Write-Host $appCert.KeyCredentials
And this is the result, what this variable has inside, we can take a look at the EndDate, that is where our Certificate will expire:
class KeyCredential {
CustomKeyIdentifier: System.Byte[]
EndDate: 8/10/2032 1:02:44 PM
KeyId: b773ba47-5614-4cf5-9d94-00b15b7fd8b7
StartDate: 8/10/2022 1:02:46 PM
Type: AsymmetricX509Cert
Usage: Verify
Value:
}
So in order to take that information only, let’s run the next command:
Write-Host $appCert.KeyCredentials.EndDate 8/10/2032 1:02:44 PM
Now we have the date when the certificate expires. We can of course automate this, send an email, or send it to InfluxDB and monitor it with Grafana, etc.
Bonus, Getting all the Enterprise Applications Certificates from a Tenant on CSV
There is currently an official PowerShell Script that it handles all of this pretty well, and after run it, it will generate a great CSV that looks like this:
![]() The script is really simple to modify, and once again send this over email every week, or to a ticketing system, etc.
The script is really simple to modify, and once again send this over email every week, or to a ticketing system, etc.
I hope this information is useful for you guys, and please do not let your Certificates expire as you might experience failing backups in the case of VBM365, and some other problems depending of the different applications.

[…] Jorge aborde le sujet d’expiration des certificats pour Veeam Backup for M365 et les Azure AD Application : https://jorgedelacruz.uk/2022/08/26/veeam-how-to-check-your-veeam-backup-for-microsoft-365-applicati… […]