Greetings friends, just a few days ago Veeam officially announced the support for MinIO Immutability on its HCL. This is wonderful news for us to test this functionality in our labs, or in case we are using Linux storage with MinIO for production. In this blog entry, we're going to jump into the pool and see: how to install and configure MinIO
veeam
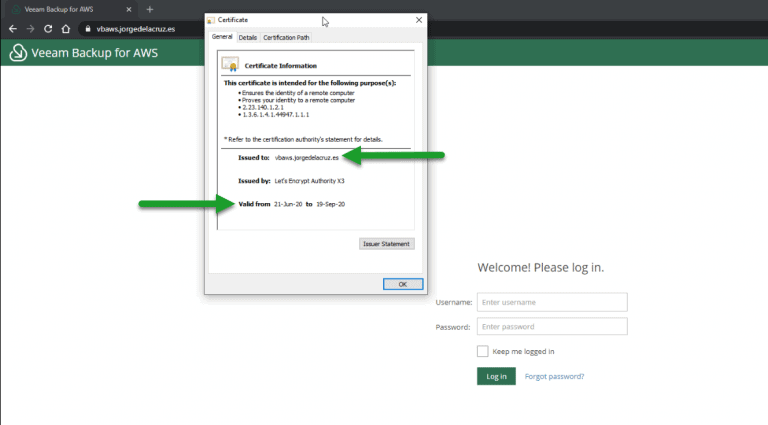
Veeam: How to Secure your Veeam Backup for AWS v2 instance with a Let’s Encrypt SSL certificate
Greetings friends, a few days ago I was showing you everything we need to know about Veeam Backup for AWS v2, in case you haven't been paying attention, I'm posting the blog here (in Spanish): Veeam anuncia Veeam Backup for AWS v2.0 - Replica de Snapshots entre Regiones, application-aware, CBT y RESTful API Today I bring you one more step
Veeam: How to connect our Veeam Backup & Replication to Veeam Backup for Azure
Greetings friends, we have already seen in the previous posts that Veeam had launched Veeam Backup for Microsoft Azure Free Edition, the solution to protect workloads in Microsoft Azure without the need of agents. Also, and as we all like it, with a free version of up to 10 Instances. In addition, we have seen how to deploy it step by step, and its
Veeam: An in-depth look at the new Veeam Backup for Microsoft Azure- Creating Backup and Restore Policies
Greetings friends, we have already seen in the previous entry that Veeam had launched Veeam Backup for Microsoft Azure Free Edition, the solution to protect workloads in Microsoft Azure without the need of agents. Also, and as we all like it, with a free version of up to 10 Instances. Besides, we have seen how to deploy it step by step, today we
Veeam: How to Deploy Veeam Backup for Microsoft Azure – step by step
Greetings friends, we have already seen in the previous entry that Veeam had launched Veeam Backup for Microsoft Azure Free Edition, the solution to protect workloads in Microsoft Azure without the need of agents. Also, and as we all like it, with a free version of up to 10 Instances. Let's see the step by step to deploy Veeam Backup for Microsoft